Boost your Hardsec deployments with turbocharged, zero-trust CDR file protection
The quest for truly robust security is like hunting for the Holy Grail. For instance, security based solely on hardware offers huge potential to provide solutions that robustly protect a trust boundary. Yet, this has practical challenges, such as its potential to limit the processing of complex data structures, thereby affecting usability.

The hybrid Hardsec approach: a new era of high assurance security
In contrast, our hybrid Hardsec approach turns the tables on traditional security methods. Adhering to the 'transform and verify' philosophy introduced by NCSC’s Pattern for Safely Importing Data, we use software to transform data types, and Field Programmable Gateway Arrays (FPGAs) to verify the integrity of data before transfer.
The NCSC’s security principles for cross domain solutions highlights 13 security principles, with two critical concerns being i) Network protocol attack protection and ii) Content-based attack protection. Glasswall zero-trust Content Disarm and Reconstruction (CDR) in combination with FPGA verification addresses both principles.
For instance, we employ Protocol Filtering Diodes (PFDs) to support one-way data transfer via hardware, while also acting as a protocol break, removing, and reconstructing headers. Unlike conventional hardware-based security systems, an FPGA chip can be reprogrammed post-manufacture, giving security teams the much-needed control to address any identified vulnerabilities.
Integrating FPGAs in Cross Domain Solutions (CDS) and other security systems dramatically improves latency compared to traditional CPUs. With FPGAs, a latency of approximately 1 microsecond is achievable - a stark contrast to the average CPU latency of around 50 microseconds. FPGAs in combination with PFDs can provide high network transfer rates.
Despite their potential, FPGAs face challenges when it comes to verifying complex data types for Cross Domain Solutions. This is where the transformation step becomes critical, allowing hardware to inspect sophisticated data structures.
Glasswall's CDR technology brings zero-trust software into the Hardsec deployment mix. Our advanced filter logically verifies data structures, removing active content and ensuring data constructs align with the manufacturer's file specification. This eliminates the risk of malicious files from reaching vulnerable software applications in the destination environment.
How Glasswall transforms files

Transform: Glasswall's zero-trust CDR technology unravels a file’s complex internal structure into a human-readable simplified SISL or XML file, representing its Document Object Model (DOM). Images are transcoded into standardised bitmaps, enabling partner technology to undertake hardware verification as recommended by the NCSC.

Verify: The simplified, human-readable data structure undergoes FPGA verification, both syntactically and semantically, and is transferred across trust boundaries by network devices such as a Protocol Filtering Diode (PFD).

Reconstitute: The verified simple data structures are reconstituted into the desired output format, providing a visually identical representation of the original file, with all threats removed.
This approach facilitates a distributed Cross Domain Solution approach. Hardware which facilitates high network transfer rates and FPGA-based verification can be concentrated at the trust boundary. Content-based attack protection, which relies on intensive compute can be parallelized so that multiple Glasswall zero-trust CDR Engines eliminate threats and transform files simultaneously using cloud-native design patterns.
Real world application
Glasswall seamlessly integrates within a UK Government Hardsec Cross Domain Solution deployment

The Challenge
Becrypt, a high assurance security vendor, were working alongside the UK government to develop a Cross Domain Solution (CDS) that could facilitate the transfer of files across trust boundaries, in compliance with the NCSC’s Pattern for Safely Importing Data.
A critical component of the NCSC’s pattern requires Cross Domain Solutions to perform hardware verification for all files travelling across trust boundaries. While offering comprehensive capability, the Becrypt Solution, known as APP-XD, did not support complex data import in accordance with the NCSC’s Pattern for Safely Importing Data.
The Solution
Becrypt partnered with Glasswall, harnessing industry-leading CDR file sanitization and transformation capabilities. The Glasswall Embedded Engine was easily integrated with APP-XD’s architecture via a secure API integration.
The Outcome
Becrypt’s High Assurance Cross Domain Solution, APP-XD, can now facilitate NCSC-compliant file transfers using Glasswall CDR technology – satisfying the UK government department they were developing the product with.
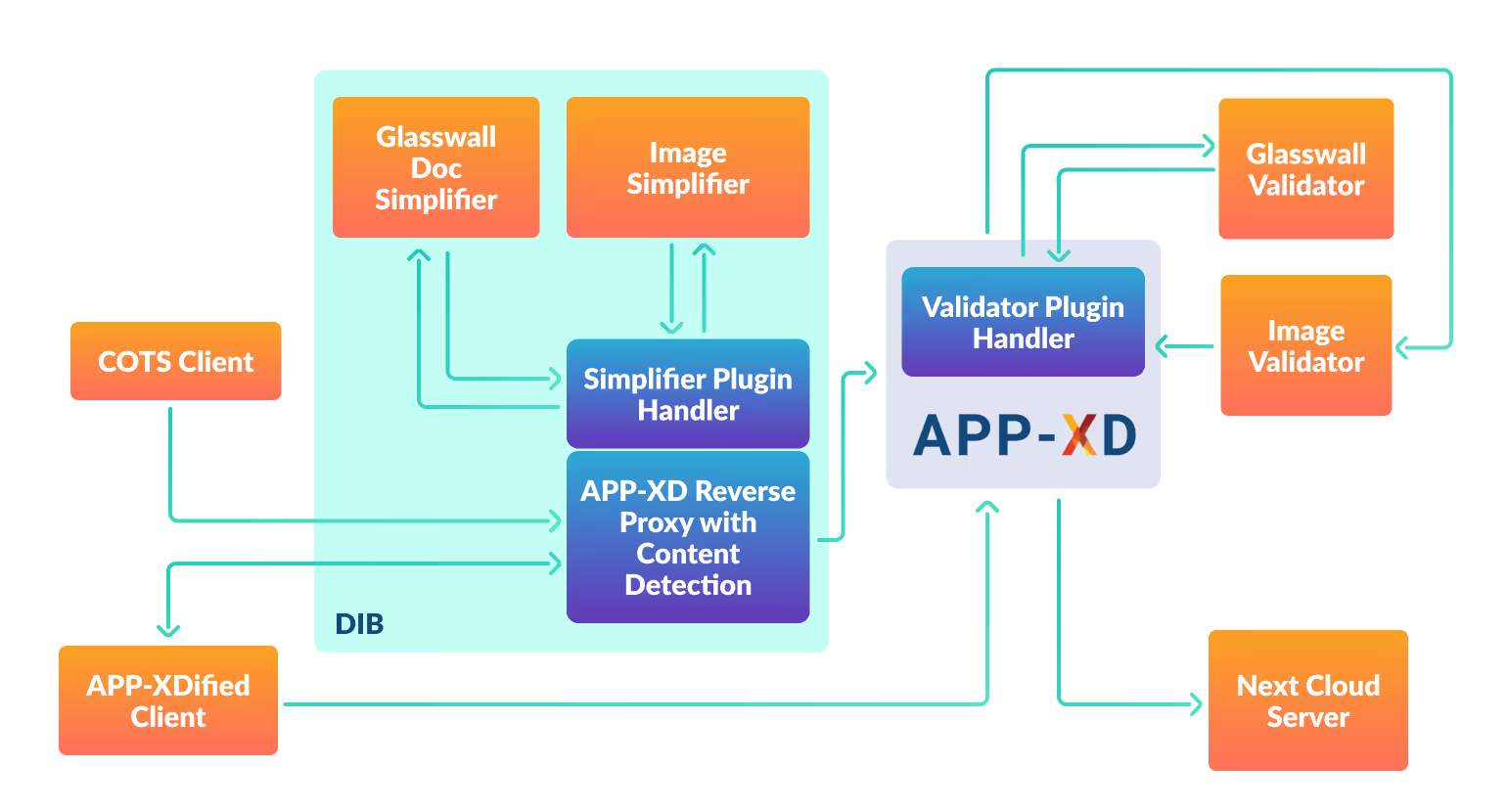
Now, once an unknown or malicious file enters APP-XD’s secure reverse proxy, the Glasswall Embedded Engine is called via the API:
- Glasswall’s Embedded Engine secures the file by performing semantic verification, validating the file against its manufacturer’s ‘known good’ structure and removing any active content present within the file.
- The Glasswall Embedded Engine then transforms the complex data type (i.e., PDF, DOCX…) into a simple and verifiable one (XML). This simple data type is sent through APP-XD’s secure gateway.
- The simple data type is syntactically verified against an XSD in hardware. This ensures only correctly formed data types are present, before being semantically verified within the Gateway.
- Glasswall’s Embedded Engine reconstitutes the simple data type back to the original, complex data type.
- Finally, before delivering the data to the destination system, Glasswall’s Embedded Engine again secures the file by rebuilding the complex file types to their manufacturer’s ‘known good’ structure, verifying, and removing any active content found. This means that only safe and fully functional files pass across the trust boundary into highly classified networks.
For a brief video overview, watch the APP-XD demo below:






.png)
