Zero-trust file security - Why pen testers and red teams should champion CDR
Offensive security, also known as ethical hacking or penetration testing, is a proactive approach to cybersecurity that involves testing digital systems for vulnerabilities and weaknesses. The ultimate goal is to identify and fix these issues before attackers misuse them. Among the foremost threats confronting organizations is the malicious manipulation of everyday files and business documents and the alarming gap that can exist in the protective measures recommended by pen testers and red teams.
In this blog, we’ll discuss the efficacy of common file protection technologies, the repercussions of relying on them, and the role of Content Disarm and Reconstruction (CDR) in a comprehensive zero-trust cybersecurity strategy.
The methods that keep falling short
We're all familiar with the scenario: a high-ranking executive receives a suspicious file, opens it unknowingly, and suddenly, the company is grappling with a major security breach. Everyday documents are at the core of business operations, and the human element in security is an unavoidable challenge. In response, security teams deploy a myriad of solutions such as antivirus software, sandboxing, firewalls, and end detection response (EDR) systems, all aimed at detecting and halting the spread of malicious actors.
Still, there's a glaring issue with all detection methodologies—they rely on prior knowledge of threats, whether through file signatures or behavioural patterns. In the following section, we’ll detail how these commonly used solutions leave organizations vulnerable to zero-day malware, file vulnerabilities and other, previously unseen attack methods.
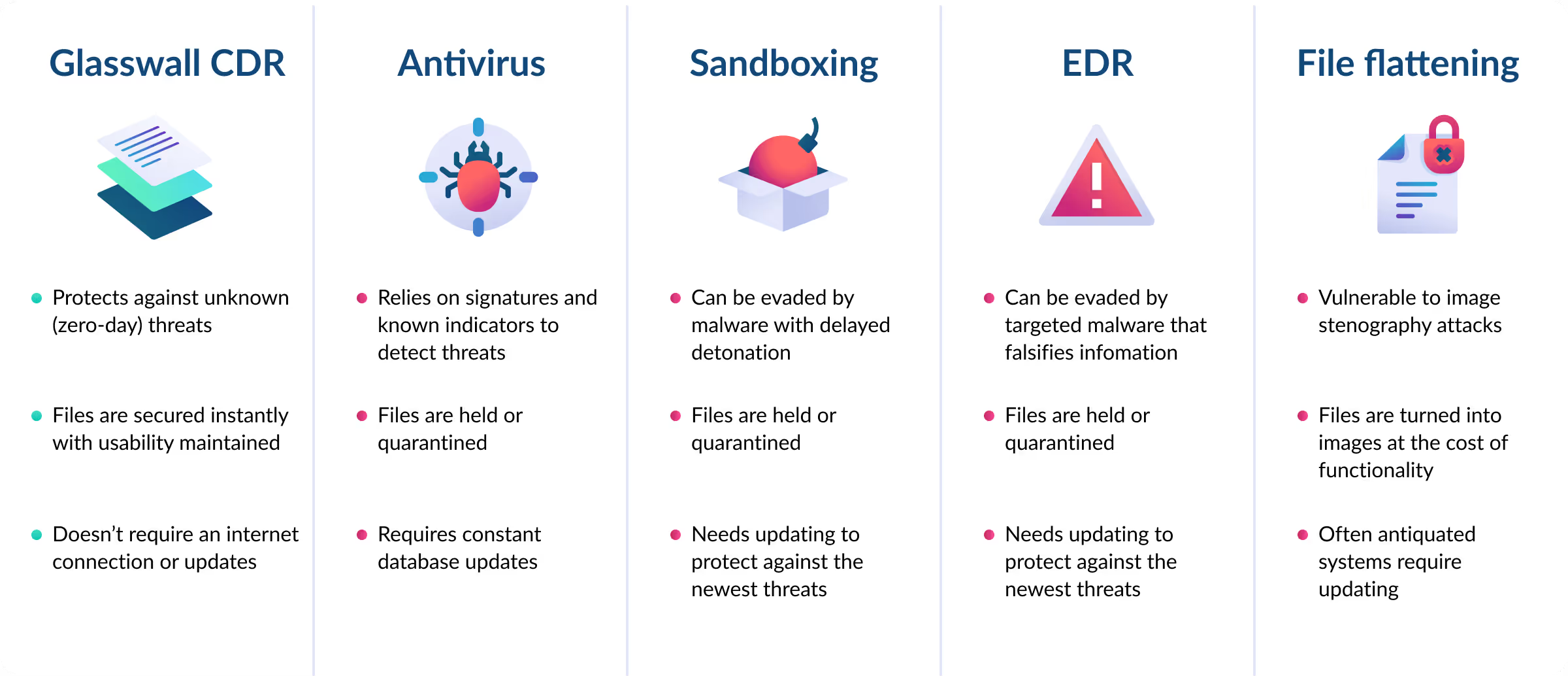
Antivirus (AV)
Antivirus software relies on signatures to identify known malware and takes an average of 18 days to discover unknown threats, and the sheer volume of over 1,111,253,431 new malware variants created last year underscores the magnitude of the challenge. For most organizations, relying solely on traditional antivirus exposes them to an unacceptable level of risk. (AVtest 2024)
Sandboxing
Sandboxing shares similar vulnerabilities with antivirus software, as its effectiveness hinges largely on its ability to detect threats within an isolated environment. To evade detection, malicious content can be equipped with ‘environment scanning’ abilities or a delayed 'time bomb', allowing malware to remain dormant and undetected, detonating only once it passes through the sandbox.
File flattening
Another strategy employed to mitigate risk, particularly in high-security government environments, involves the utilization of file-flattening data filters. These filters transform documents into images, essentially flattening them at the expense of all file functionality. These systems are often antiquated and are vulnerable to image steganography, where information can be concealed in such a way that it deceives the viewer. Some of these methods attempt to transform the image back into a file, causing structural issues and exposing further exploitable vulnerabilities.
Endpoint Detection and Response (EDR)
EDR systems are designed to detect malware that targets network-connected devices by monitoring endpoint activity and identifying threat patterns. It is well known that malware developers are able to tailor their work to specifically evade EDR, and this is a growing issue in cybersecurity communities. Techniques such as ‘Hook Overwriting’ and ‘CPL Side-Loading’ can shield malware from detection by intercepting and falsifying data collected about a program's behaviour. (Malware tech 2023, White knight labs 2024)
This perpetual cycle of innovation and countermeasures underscores the reactive nature of cybersecurity, where adversaries continually develop more sophisticated weaponry, prompting defenders to adapt and fortify their defences in response. This results in a game of cat and mouse.
CDR - The zero-trust approach
Glasswall CDR embraces the zero-trust paradigm of “never trust, always verify”, which has revolutionized much of the cybersecurity world. Instead of looking for malicious content, our solution treats all files as untrusted, validating, rebuilding and cleaning each one against its manufacturer’s ‘known-good’ specification. As a result, only safe, clean, and fully functioning files can enter a network, allowing organizations to access them with full confidence.
Our out-of-the-box CDR solutions come ready to implement via APIs, and are used to secure all types of trust boundaries such as Cross Domain Solutions and file upload portals. Additionally, our CDR offers analysis of the threats within files with comprehensive risk reporting and empowers security teams to remove or manage high-risk content according to their risk appetite.
Adding CDR capability to an organization’s security stack plays a vital role in a rounded zero-trust cybersecurity strategy and should be a consideration for Pen Testers and Red Teams looking to recommend mitigations. In 2021, Gartner set out their recommendation in the fight against malicious files as follows:
“Restrict file types to the minimum required. For allowed file types: CDR provides the highest security. Done well, CDR removes all threats from files without adding significant latency. Since it does not depend on the detection of known threats, it can even protect against completely new attack types.”

Trusted by the world’s most secure agencies
Glasswall zero-trust CDR is an NSA-mandated file filter and is being adopted as a frontline defense by the world’s most sophisticated security agencies. A benchmark test conducted by a governmental partner showed Glasswall CDR surpassed seven other leading antivirus and Cross Domain Solutions across a wide range of tested file types. Our technology also helps organizations to comply with initiatives such as the NSA's Raise the Bar and NCSC's Pattern: Safely Importing Data.
Protection without compromise
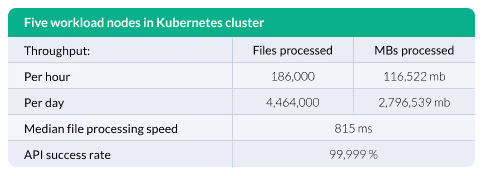
Glasswall CDR can secure files at rapid speed and massive scale. With an average file processing time of just 815 milliseconds, and five workload nodes processing 4.4 million files per day (or 2.7 million MBs of data), organizations who harness the power of the Glasswall no longer face a security for speed trade-off. See the results of our most recent performance test below.
Glasswall Halo v2 Performance Test Findings:
File configuration:
- 20 business files ranging from 17 MB to 0.05 MB in size
- File types include: PowerPoint, Video, Excel, Word, Image, PDF, Audio
- Median file size = 0.64 MB
Technical assumptions:
- 5 Engines per node
- 8 virtual cores
- 28 GB Memory
- Request concurrency to availability of resource is 1:1
Test results:
Small print:
- Throughput may vary dramatically based on the size and complexity of each file.
- We have opted for conservative metrics by assuming that the median file size is less than one 1 MB.
- Infrastructure constraints such as storage I/O speeds may impact observed speed.
- A concentration of larger media files may lead to significantly higher throughput.
- Real throughput will always be constrained by the licence entitlements purchased.
- A higher request concurrency to available CDR resources will lead to higher throughputs of files but may result in lower processing times per file.
About Glasswall:
Glasswall is a cybersecurity company that protects government agencies and commercial organizations from malicious files with its Content Disarm and Reconstruction (CDR) technology. Unlike traditional detection-based methods, Glasswall employs a zero-trust approach, which removes the ability for malware to exist in files altogether.
Talk to our team to find out more, or try cleaning a file with our ad hoc file cleaner.







.png)
