Glasswall CDR Removes Hidden Malware in SVG Files Without Disrupting Content
Recent attack campaigns have leveraged SVG smuggling techniques to achieve phishing objectives against targets. SVG-style attacks typically involve using the XML structure to redirect a user to an offensive domain for credential harvest, execute malicious JavaScript and, in most recent instances, create interactive fields for credential theft.
Variations to an old theme
SVG is an XML based file format which is used to present graphics typically via web browsers. As the format is in XML it can contain arbitrary attributes and fields which are used by malicious actors to hide payloads and other unwanted content. SVG interpreters also have the capacity to run JavaScript code, which may be embedded in SVG image files, making them a potential security concern.
Older SVG-based attacks would typically do one of two things: embed JavaScript within the XML to execute upon opening of the file to exploit a vulnerability in the browser or, upon opening the file, redirect the browser to open a webpage at a malicious domain, potentially allowing credential harvest. Newer attack methods disclosed by the MalwareHuntingTeam[1] show other techniques where SVG files may themselves perform the credential harvest. This is achieved via encoded interactive fields being rendered upon opening and being interactive with the end user. These typically involve social engineering to the theme of “the document is locked, and user credentials are required to unlock”. Upon clicking unlock, the fields populated by the user are transmitted to a malicious domain for collection rather than full redirection to malicious domains seen in older techniques.
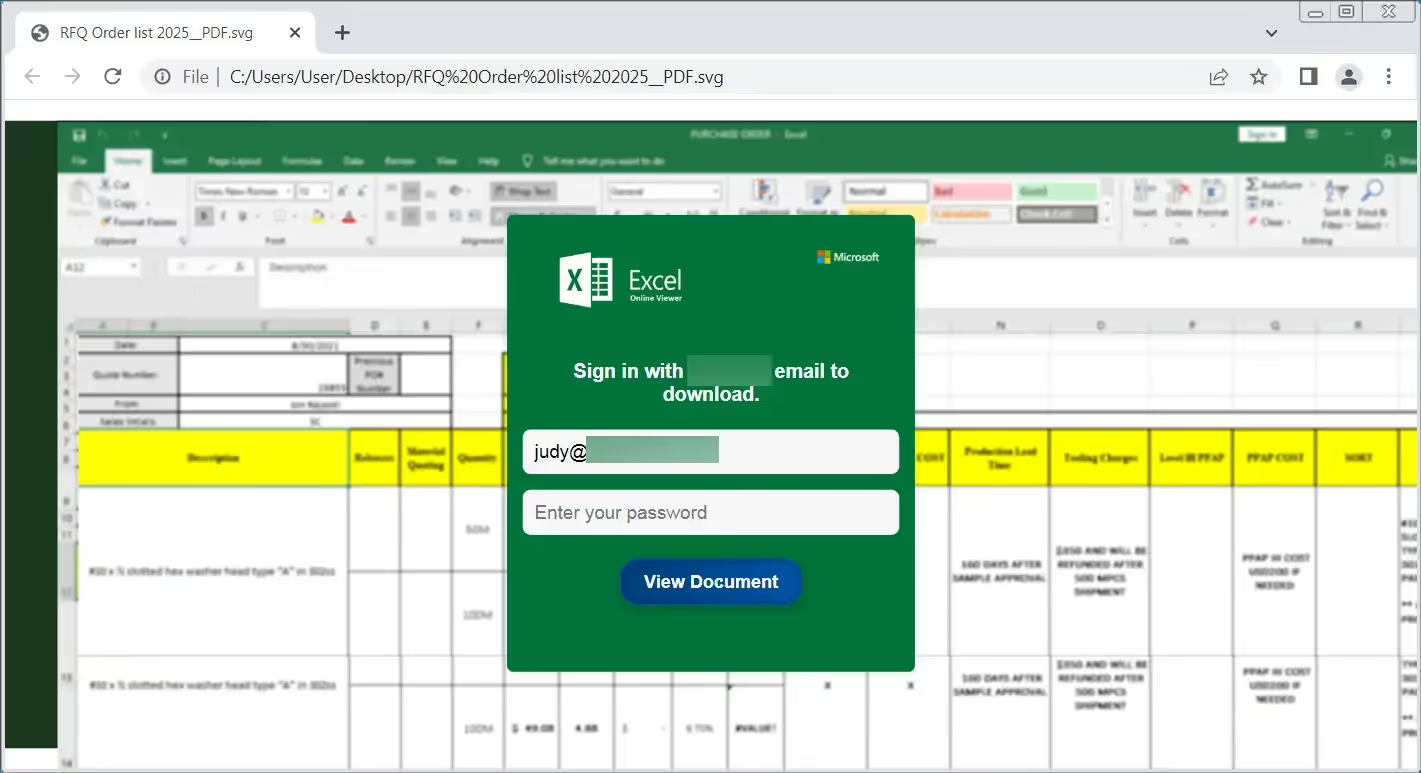
CDR squashes unwanted SVG content
Glasswalls CDR technology active scans all SVG files and detects the presence of unwanted components such as JavaScript or elements such as “foreignObjects” which are commonly used for malicious purposes to hide content. As standard, the CDR process is able to dissect, analyse and remove these elements whilst leaving the image data intact for user access. Effectively, this retains all the image data but removes any interactive and potentially malicious elements within the SVG structure.
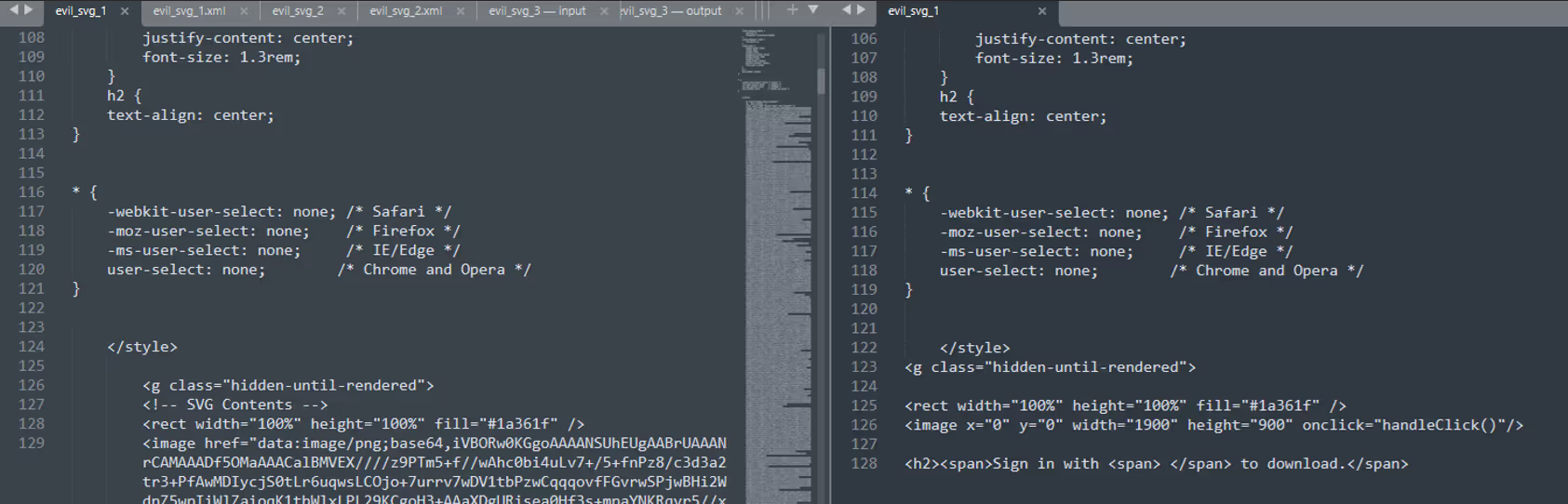
In the example above, an in-the-wild sample is subjected to Glasswalls CDR process and the class containing the encoded malicious interactive fields is removed during the remediation process of the file. The result is an SVG file with all JavaScript and foreignObject data removed, eliminating elements commonly used for malicious operations and in this use-case cleaning the file of any threats.
Sources


.avif)




.avif)

