5 things to consider when choosing a CDR vendor
It has become evident in recent years that traditional cyber-security solutions alone can no longer adequately protect organizations in today’s threat landscape. 80% of breaches result from zero-day (unknown) attacks and many organizations are searching for a proactive zero-trust solution to replace their existing reactive systems.
Why choose CDR?
CDR (Content Disarm and Reconstruction) is different to other security technologies. Instead of looking for malicious content, CDR treats all files as untrusted – processing each file to a safe standard that automatically removes potential file-based threats.
CDR allows only safe and clean files to enter and leave an organization, enabling users to access them with confidence.
Gartner has penned CDR as the number one file protection solution:

Top five considerations when choosing a CDR provider:
There are a number of solutions on the market, but not all are created equal. There are some crucial considerations when choosing a CDR solution.

1 – Are all file types fully functional once they have been processed?
When choosing a CDR vendor, it is important to investigate which solutions process file types in their intended format and which don’t. There are a number of technologies on the market that lack the capability to process a wide range of file types in their intended format. To overcome this, and to provide support for as many file types as possible, files are transformed into a simple flat file type, such as a JPEG image file, allowing for it to be processed by the vendors CDR technology and made safe.
However, the process of file flattening strips the file of its original functionality, in many cases removing its useability altogether. This reduces a user’s ability to work collaboratively on a document, disrupting their workflow and reducing workplace productivity.
In addition, many CDR vendors have an extensive list of supported file types – and while that may be impressive upon a first glance, a closer inspect often finds that few are processed in their intended file type. This isn’t always clear from a vendor’s market facing content, so when reviewing vendor options ensure that a distinction is made between which files their technology truly CDRs, and which file types are flattened to enable processing to take place.
Where Glasswall fits:
Glasswall’s patented CDR technology processes files in their intended file type. This ensures that all files processed by the Glasswall Embedded Engine are safe, clean and fully functional – there is no need to compromise by using flattened files.

2 – Does the vendor use manufacturer recommended libraries to reconstruct a file?
The rebuilding of a file is an integral part of why CDR is considered the best defence against file-based threats. This stage of the CDR process uses libraries to rebuild a file back to a secure standard.
However, when selecting your CDR vendor, it is important to consider which libraries are being used to rebuild files. It is common for CDR vendors to utilise non-proprietary libraries to rebuild files. While this removes malicious content hidden within the original file structure, these can still leave vulnerabilities hidden within the processed document structure – leaving your organization at risk even when a file has been processed.
Where Glasswall fits:
To achieve the best protection possible from your CDR vendor you should look for a solution that utilizes known-good specifications to rebuild files.
Our patented CDR technology utilizes manufacturer’s specifications to rebuild files back to a known-good standard. This completely removes the potential for processed files to retain vulnerabilities that leave organizations at risk from the exploitation of document structures.

3 – Can the vendor report on all non-conforming parts of a file?
Many CDR vendors in the marketplace lack the capability to provide granular reporting on the threats found while processing a file. Without this information, security teams are unable to collect intelligence about the risks facing their organization, which can lead to information fragmentation and ultimately blind spots in their wider cyber defences.
Legislation in various places around the globe requires organizations to report on the mitigating actions they have taken to remove the risk cyber threats pose to them – without granular reporting this can become a headache for security teams because they have to reprocess an original file to understand the risks included within it.
Where Glasswall fits:
Organizations assessing CDR vendor options should look for a provider that can report, in granular detail, on all the non-conforming components of a file.
With Glasswall CDR real-time processing, insights are provided as part of an in-depth report that details the changes that have been made to a file to ensure it conforms to the required known-good manufacturer’s specifications. If the file cannot be processed, the reason for this is detailed to the user.
This provides security teams with a better understanding of the threat landscape facing their organization, as well as risk reports to aid compliance with cyber security legislation.

4 – Can the vendor handle large scale data processing?
Whether you are processing a number of files from a local device or from large storage containers prior to, or during, a data migration, it is important to consider if the CDR vendor you are reviewing is capable of processing data at the degree of scale you require. While most CDR vendors boast scalability to some degree, the key differentiator within the marketplace is performance while processing at scale. To impact business-as-usual operations as little as possible, your chosen CDR solution’s performance should be maintained across large scale projects.
Where Glasswall fits:
It is important to ask your CDR provider for performance statistics both for small throughput and throughput at scale. Any reputable CDR provider should be able to provide performance statistics from their latest builds – our Glasswall CDR Platform’s latest average performance statistics are as follows, and are based on five modestly-sized virtual machines working in concert:
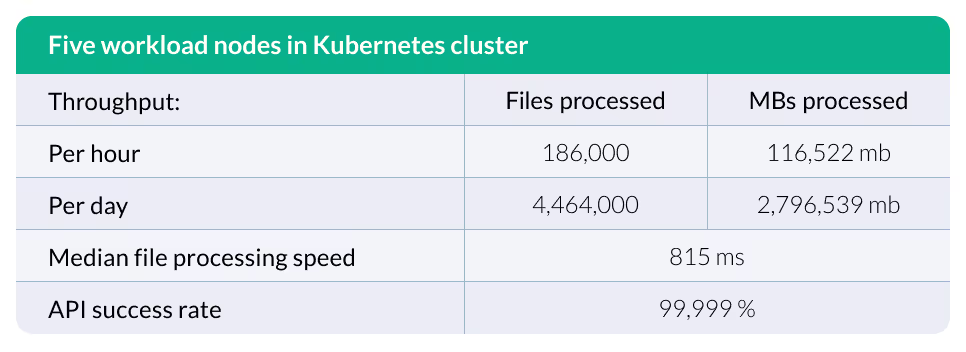

5 – Has the CDR technology you are considering been tested in the field?
Look for a CDR vendor who has a proven track record working with government and defence agencies and commercial organizations working in regulated sectors. If they have a successful record of providing file sanitization capabilities to these complex and technically demanding organizations, they should be willing to share evidence of their success. Steer clear of organizations who make claims about their capabilities and successes but are unwilling to provide any supporting evidence.
Where Glasswall fits:
Like all companies that work with sensitive clients, we are unable to disclose precise details of individual organizations and government departments that we work with. However, at Glasswall we have a history of successfully serving government and defence departments and commercial organizations around the globe with file protection capabilities wherever a file is in motion, or at rest. Our future-proof and patented CDR technologies extend into tomorrow’s threat landscape, and we are able to provide prospective customers with evidence of successful implementations across a wide range of organizational types and environments.
We can also evidence how our CDR technology helps organizations to align with the NCSCs Pattern for Safely Importing Data, the NSA’s Raise the Bar and the NIST Risk Management Framework that have been designed to help government departments, and commercial organizations, to comply with industry best practice guidelines.




.png)


.avif)